Integrating Kubernetes with Key Manager Plus
Kubernetes (K8s) - Kubernetes is an open-source platform that automates containerized application deployment, scaling, and management. Containers are a lightweight way to run applications, and Kubernetes manages them at ease by handling tasks like load balancing and rolling updates.
Kubernetes Secrets - Kubernetes secrets provide a secure way to store sensitive information within a Kubernetes cluster. It is a prominent feature of Kubernetes that ensures secured storage of secrets, such as passwords, tokens, SSL certificates, and keys in the Kubernetes cluster.
The infrastructure of Kubernetes enables the secure management of Kubernetes secrets, allowing users to manage the sensitive information required for their applications. As a result of this integration, Key Manager Plus now offers the capability to manage Kubernetes TLS secrets, including their rotation and updating based on expiry and necessity.
Note: The term TLS Secret mentioned in this document represents the SSL certificates stored in the Kubernetes cluster.
Refer to the sections that follow to learn more about Kubernetes integration with Key Manager Plus:
- Benefits of Kubernetes Integration with Key Manager Plus
- Configuring Kubernetes in Key Manager Plus
- Managing TLS Secrets via Key Manager Plus
- Limitations
1. Benefits of Kubernetes Integration with Key Manager Plus
- Collaborate on the management of Kubernetes TLS secrets in your enterprise
- Fetch TLS secrets from Kubernetes clusters and manage them in Key Manager Plus
- Manage TLS secrets from multiple Kubernetes clusters, including updation/rotation
2. Configuring Kubernetes in Key Manager Plus
To begin the configuration process, you must first download the YAML file from the Key Manager Plus interface. The YAML file is a configuration file that contains the necessary commands that must be applied to the Master node of the Kubernetes server. To download the YAML file, do the steps that follow:
- Navigate to SSL >> Kubernetes >> Manage.
- On the page that appears, click Download YAML File to proceed.
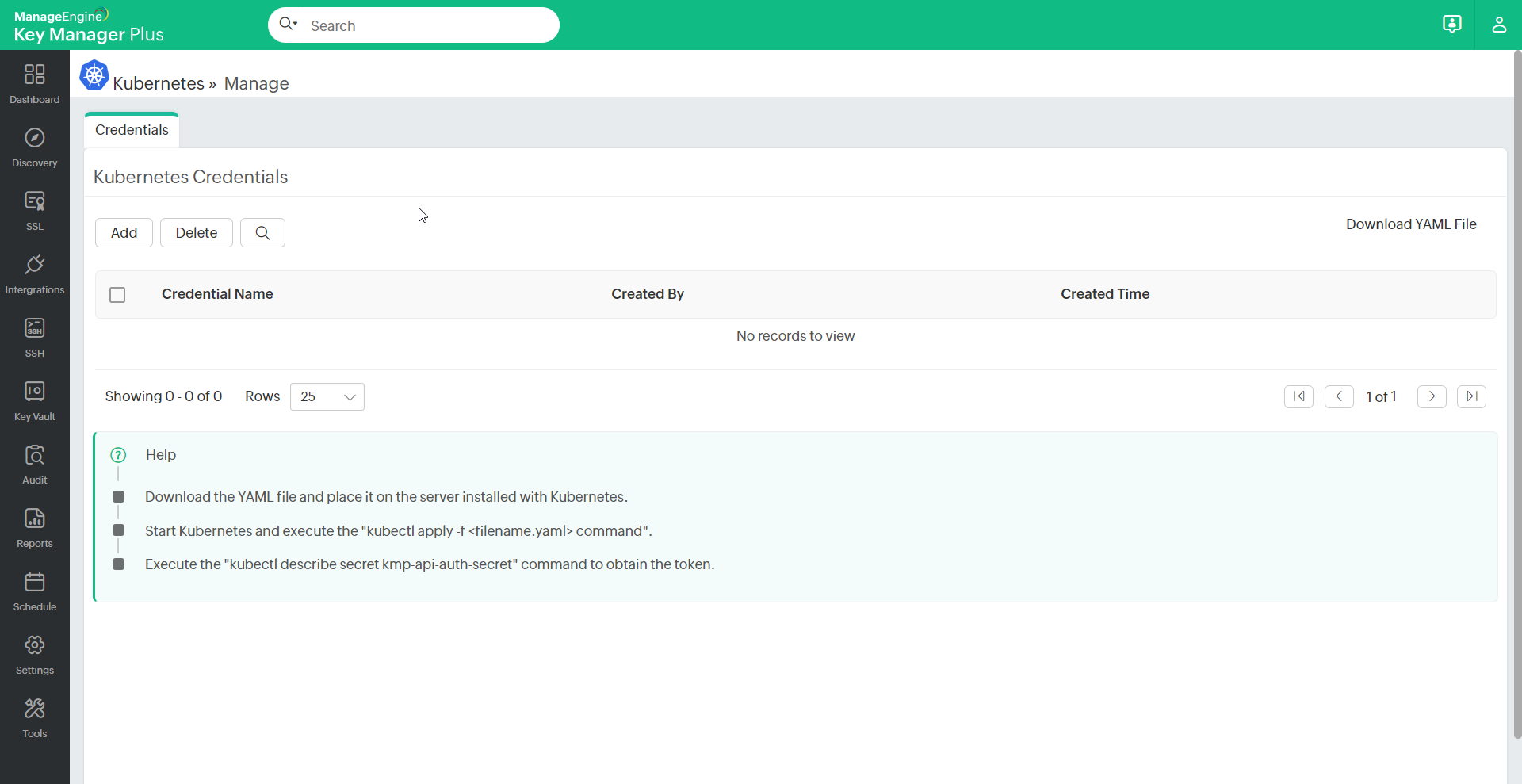
Once you have downloaded the YAML file, move it to the server where Kubernetes is running. To do so:
- Make sure that the Kubernetes server is started and running.
- Execute the following command to invoke the YAML configuration file into the Kubernetes server- "kubectl apply -f <filename.yaml>".
- This command will create a new token to authenticate the communication between Key Manager Plus and the master node.
- Now, execute the following command to fetch the token from the Kubernetes server - "kubectl describe secret kmp-api-auth-secret".
- A token will be generated post the above process. Copy or save this token value to configure the Kubernetes integration in Key Manager Plus.
Now, open the Key Manager Plus interface and do the steps that follow to add the Kubernetes clusters available in the Kubernetes server into the Key Manager Plus:
- Navigate to SSL >> Kubernetes >> Manage.
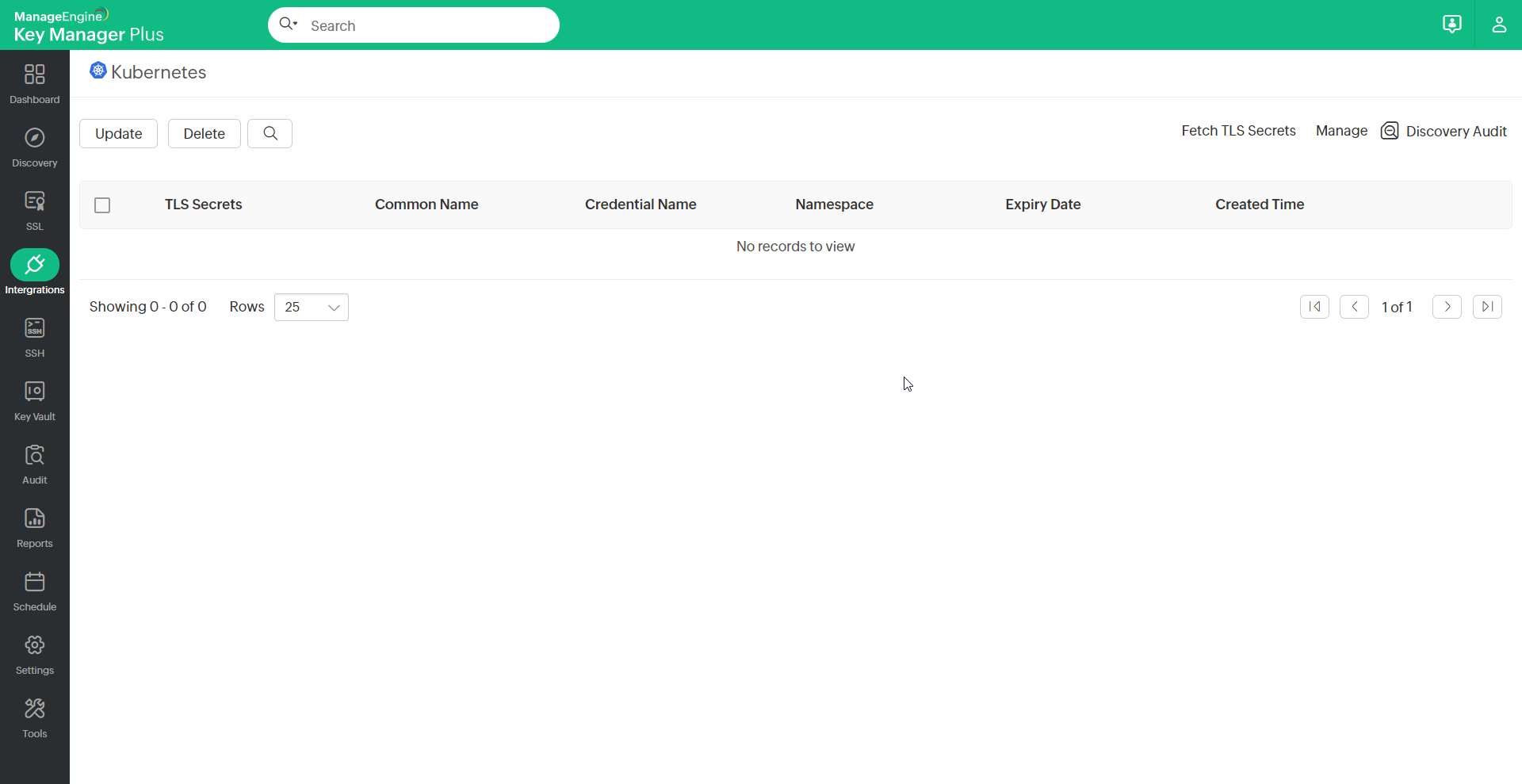
- On this page that appears, click Add.
- In the pop-up that opens, enter a Credential Name, Server URL, and Token.
- Credential Name - Enter the name of your choice to identify the respective Kubernetes Clusters. E.g., Kub Cluster 1
- Server URL - The URL where the Kubernetes server is running. E.g., http://20.XX.XX.XXX:6445
- Token - Enter here the token generated from the Kubernetes server.
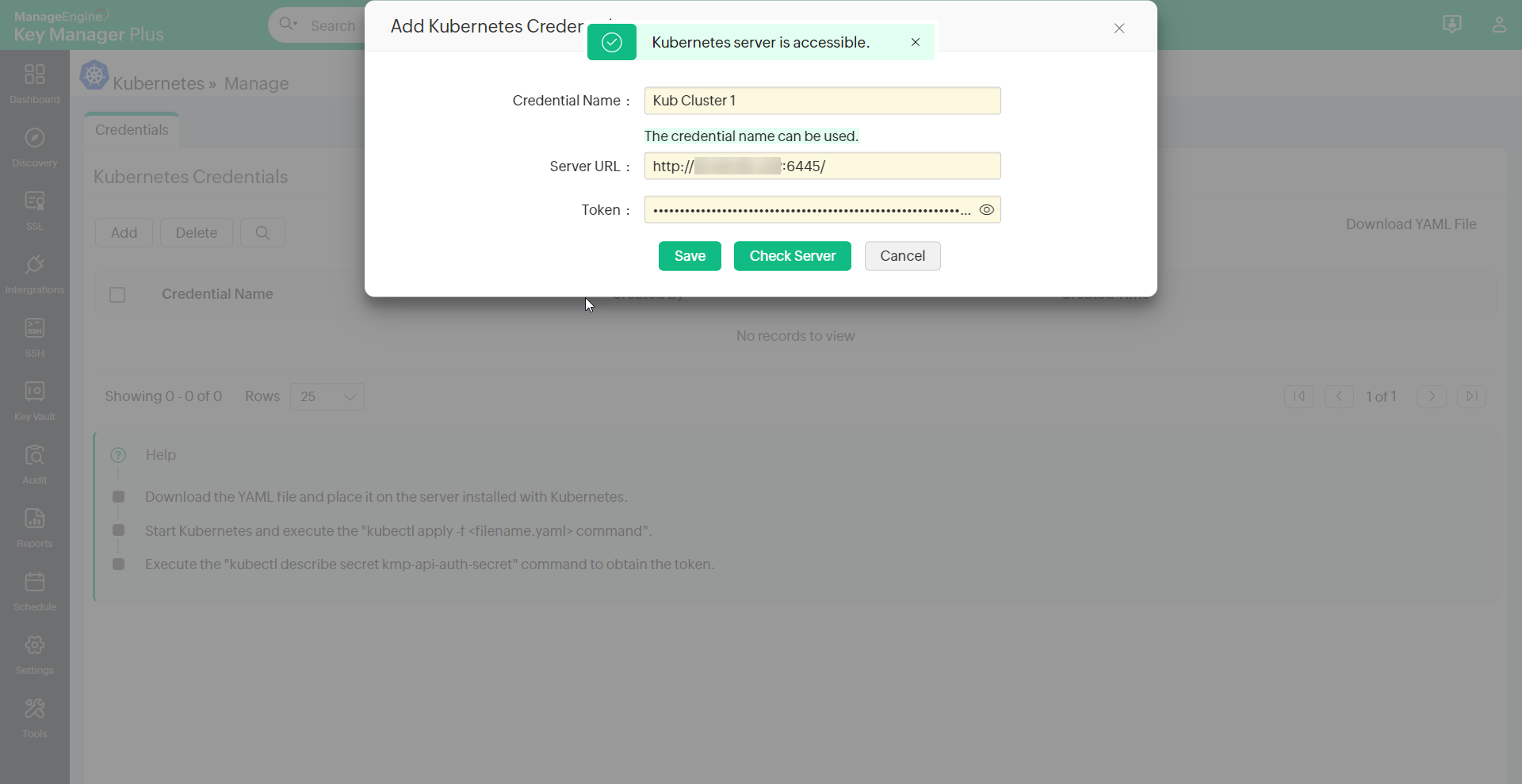
- Now, click Check Server. This operation will validate the establishment of communication between the Kubernetes server and the Key Manager Plus.
- Click Save to complete the integration process. You can save the details only if the Kubernetes server is reachable to the Key Manager Plus.
- Further, you can also delete the added Kubernetes credential using the available Delete option as required.
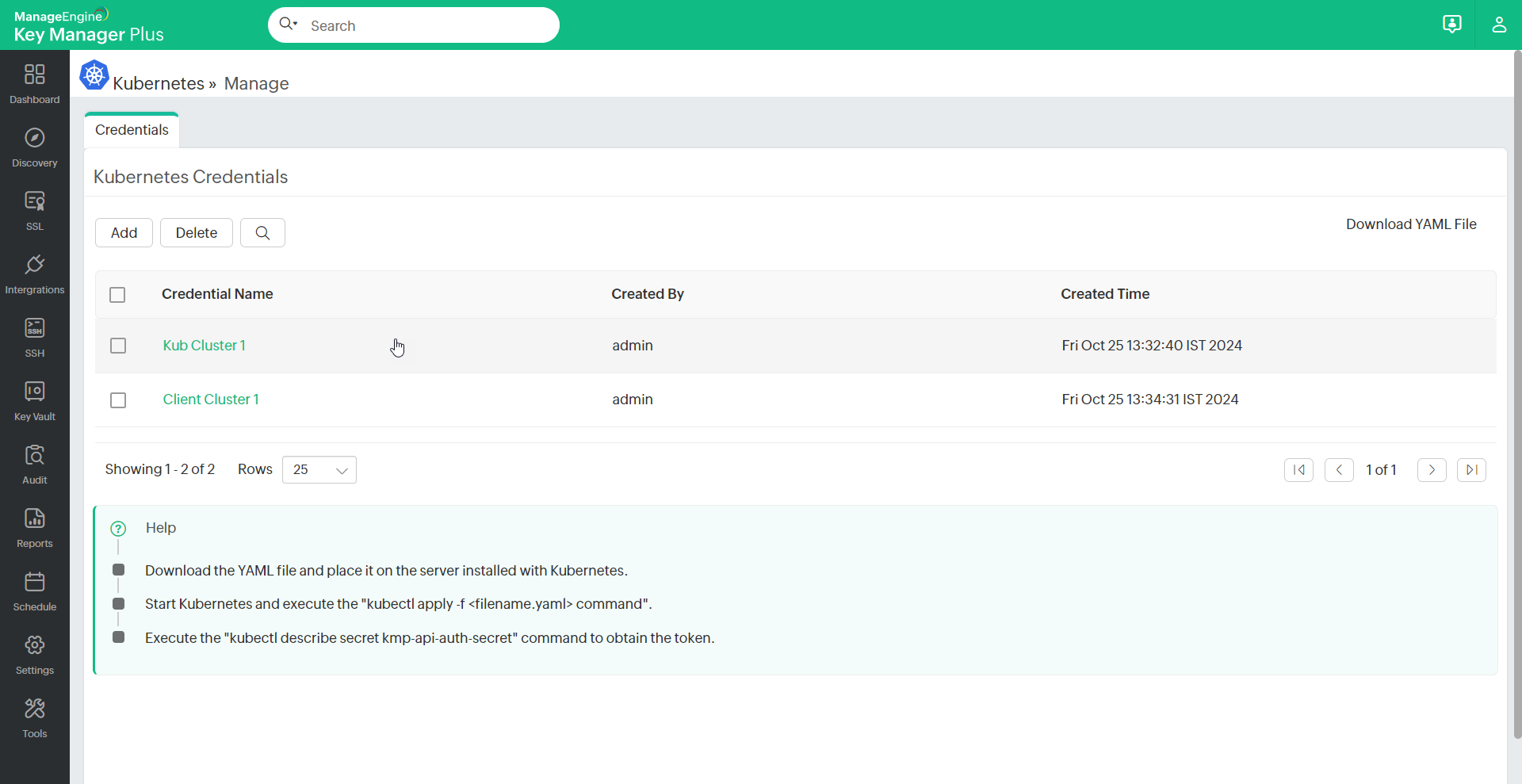
Notes: The term Kubernetes credential mentioned here in this document represents the Kubernetes cluster added into the Key Manager Plus from the Kubernetes server.
3. Managing TLS Secrets via Key Manager Plus
Once you have added the Kubernetes credential into the Key Manager Plus, you can perform four main operations with the added Kubernetes credential to manage the TLS secrets.
i. Fetch TLS Secrets from Kubernetes Credential
To fetch all the TLS secrets available in the Kubernetes credential into the Key Manager Plus, follow the below steps:
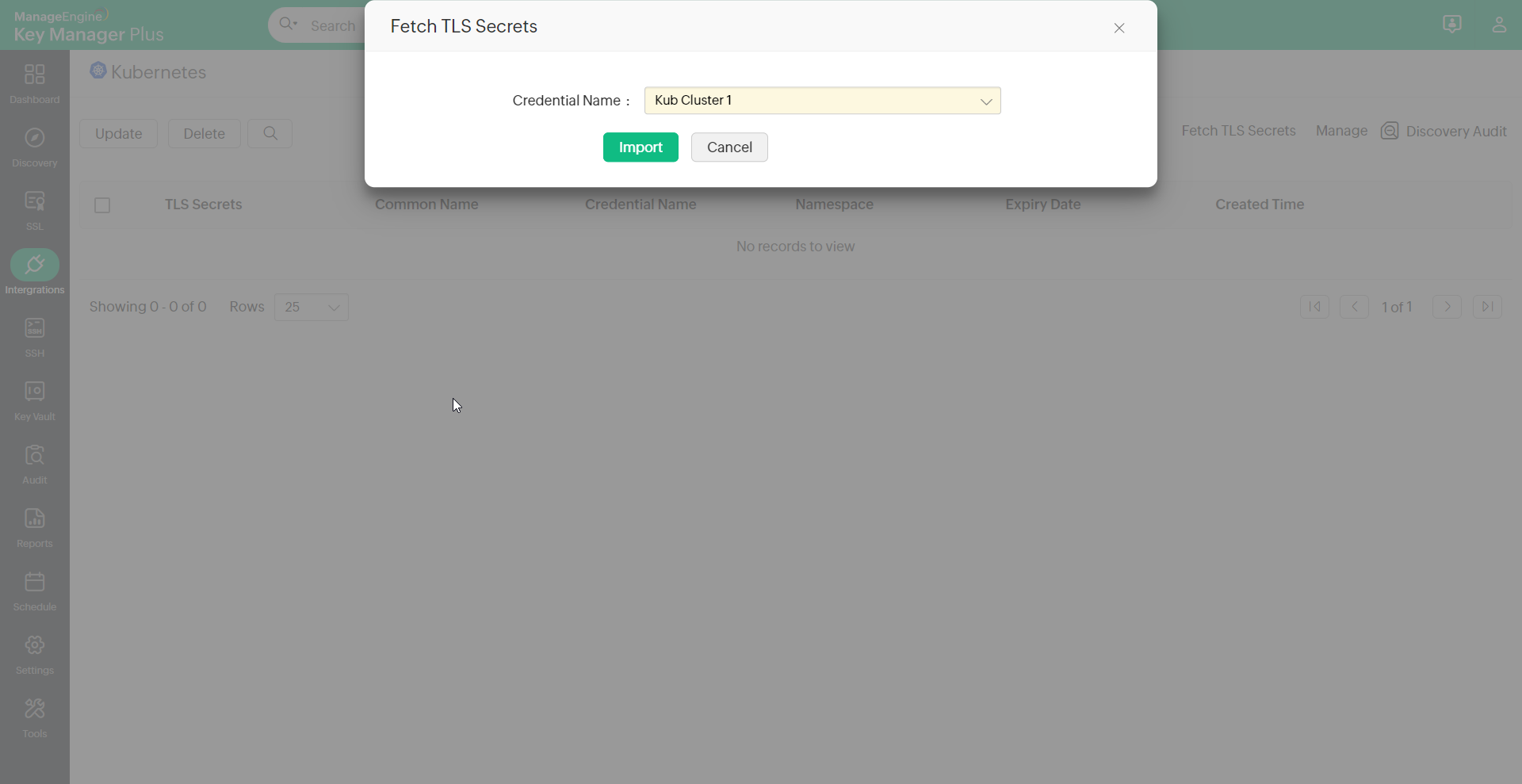
- Navigate to SSL >> Kubernetes and click Fetch TLS Secrets.
- In the pop-up that opens, select the required credential from where the TLS secrets are to be fetched and click Import.
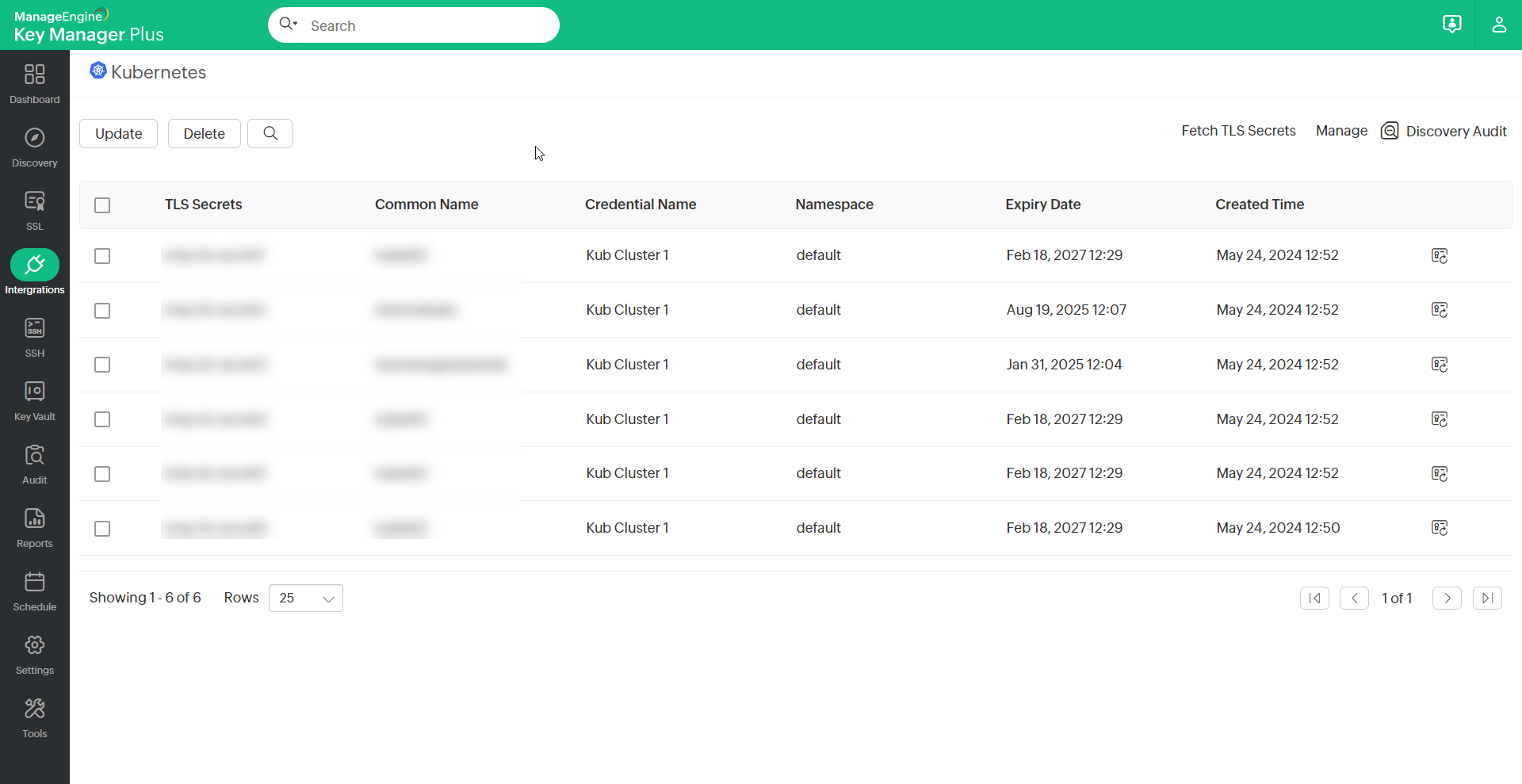
- Now, from the selected Kubernetes credential, all the available TLS secrets will be fetched with the relevant information that includes the Credential Name (Kubernetes cluster name), Common Name, Namespace, Created Time, and Expiry Date.
ii. Update TLS Secrets from Key Manager Plus
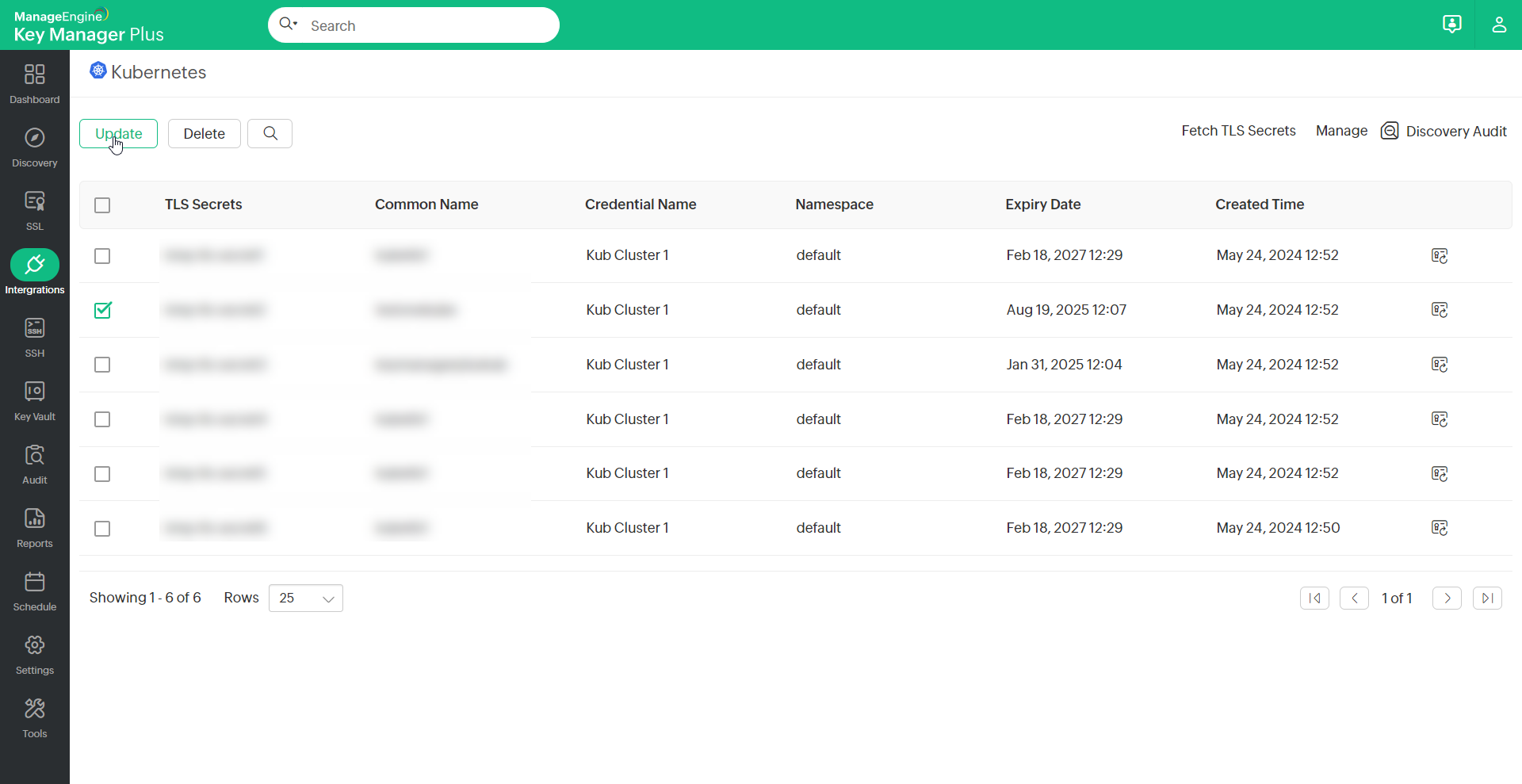
If you have an expired or about-to-expire TLS secret in a Kubernetes credential, you can update it using the available Update option in the Kubernetes window. To update a TLS secret, do the steps that follow:
- Select the TLS secret that has to be updated and click Update.
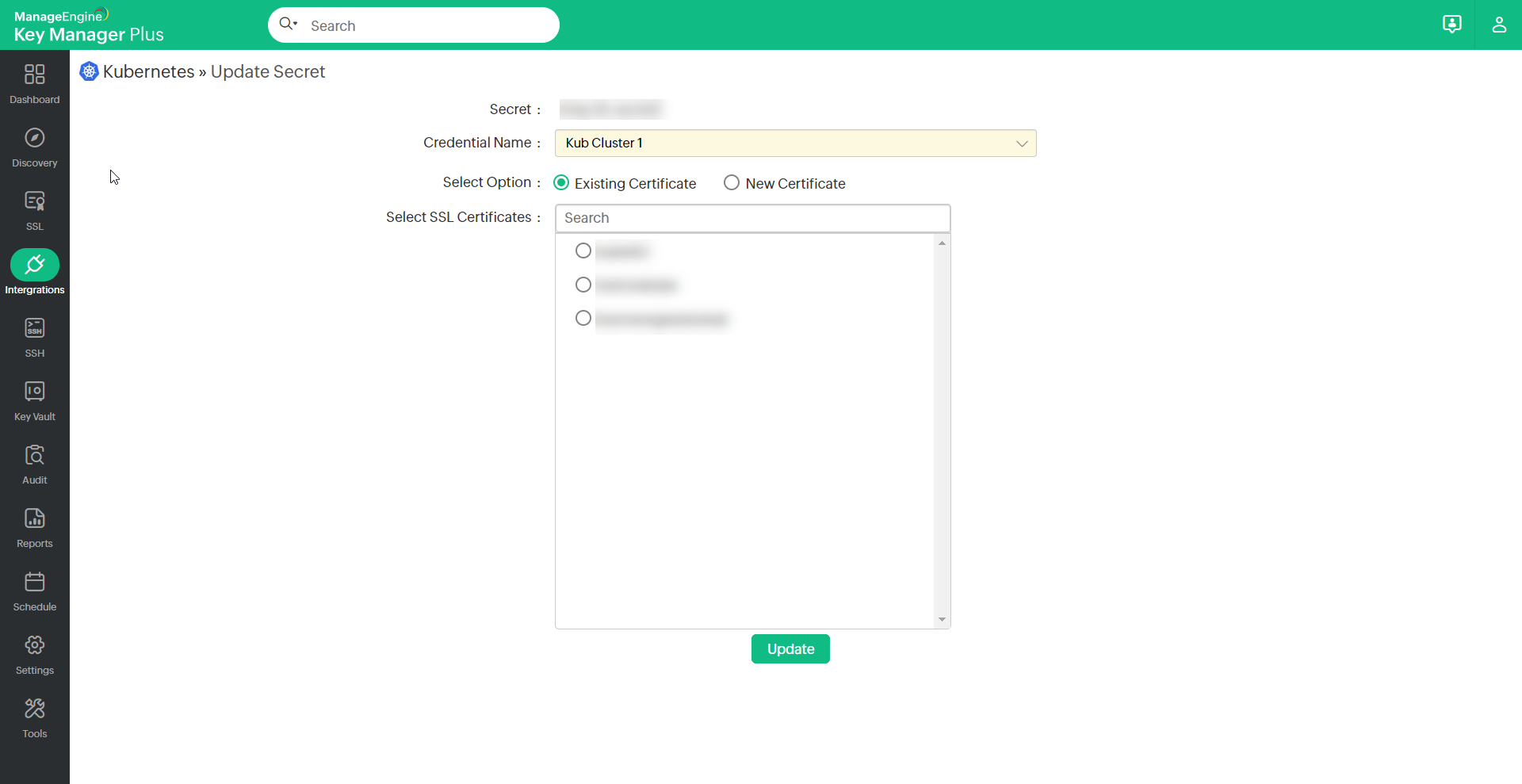
- On the page that opens, select the Kubernetes credential to which the secret has to be updated with the new TLS secret.
Notes: The update operation performed in the Key Manager Plus repository will automatically update the TLS secret in the respective Kubernetes credential (cluster).
- If you have an SSL certificate available in your Key Manager Plus' Kubernetes repository:
- Click Existing Certificate from the Update Secret window.
- Select the respective SSL certificate from the available list.
- Click Update to update the TLS secret.
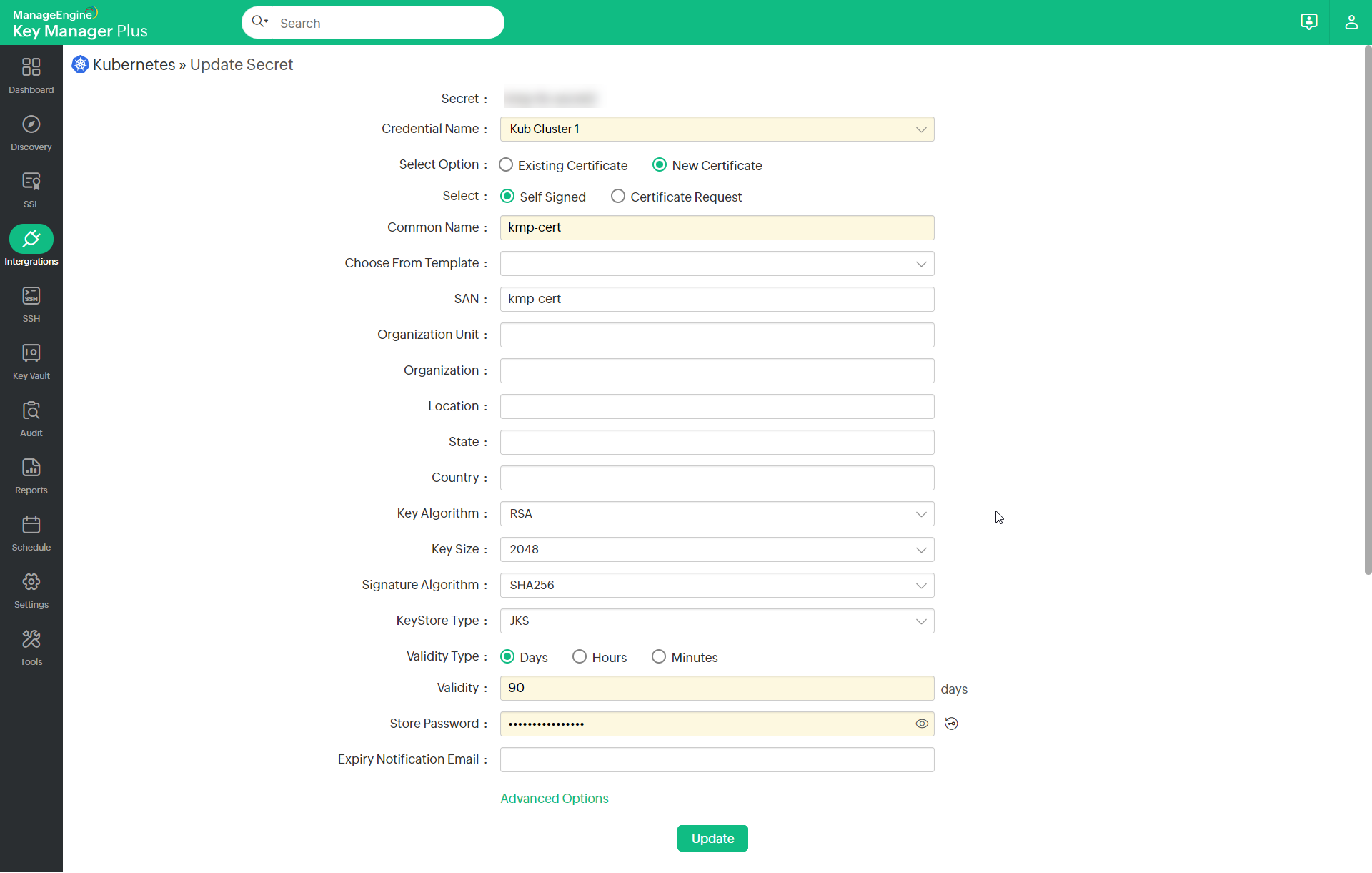
- Using the New Certificate option, you can also create new certificates using the Self-Signed or Certificate Request method.
- If you want to create a new self-signed certificate as your TLS secret:
- Click Self-Signed from the Update Secret window.
- Enter the required fields such as Common Name, Key Algorithm, Key Size, Keystore Type, Validity Type, Validity, and Store Password, and click Update.
- You can also select advanced options and enable the necessary field from the Key usage and the Extended Key Usage as per your TLS secret requirements.
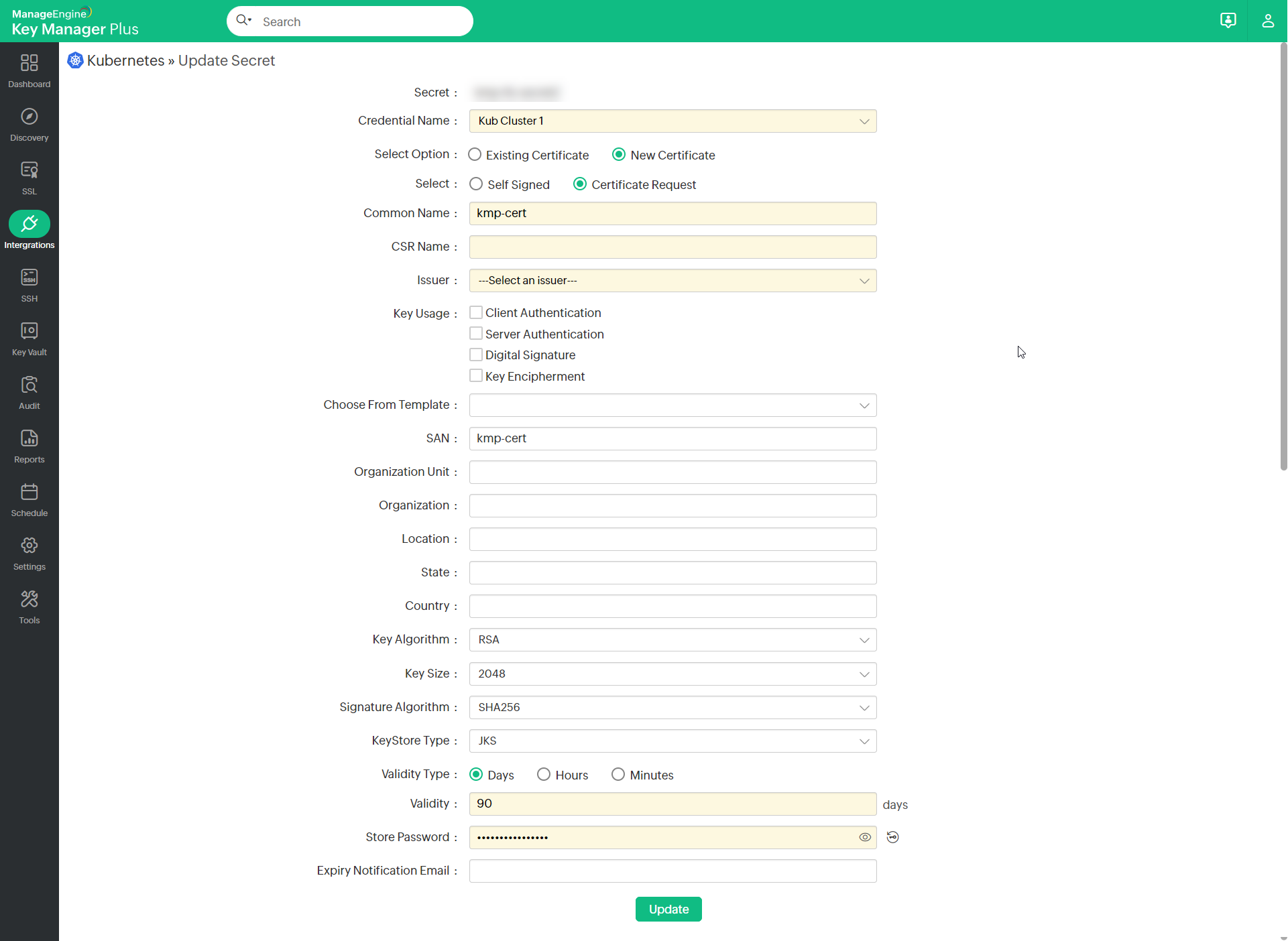
- If you want to create a new certificate as your TLS secret signed by the Kubernetes cluster Certificate Authority (CA), follow the below steps:
- Click Certificate Request from the Update Secret window.
- Enter the required fields such as Common Name, Key Algorithm, Key Size, Keystore Type, Validity Type, Validity, and Store Password.
- In the issuer field, select the respective Kubernetes cluster CA who signs the certificate based on your Key usage requirement.
- Now, click Update to get the new certificate through the created request.
iii. Delete TLS Secrets from Key Manager Plus
Select the respective TLS secrets and click Delete to remove them from the stored Kubernetes credential in Key Manager Plus. To add the TLS secrets back, you must follow the above steps. Please note that the Delete operation will remove the secret only from the Key Manager Plus repository and not from the Kubernetes cluster. We recommend you delete the TLS secret manually in the Kubernetes cluster if required.
iv. Sync TLS Secrets
In the event that a new set of secrets is introduced to the Kubernetes cluster, it is necessary to perform a manual fetch operation to maintain synchronization between the Kubernetes cluster and the Key Manager Plus. This operation will retrieve all additional secrets that were added subsequent to the initial fetch operation in Key Manager Plus.
4. Limitations
- The Key Manager Plus can only retrieve TLS secrets added to the Kubernetes cluster upon fetch. But it cannot delete/add TLS secrets that have been removed/added from/to the Kubernetes server post fetch. To keep the Kubernetes and the Key Manager Plus repository in sync, a manual fetch is to be performed as and when required.
- The Key Manager Plus does not have a built-in feature to sync with the Kubernetes server automatically at scheduled intervals.