- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing More..
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing More..
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports More..
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing More..
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer More..
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
The primary purpose of auditing network logs is to discover events of interest, whether they provide general information or call for further investigation. EventLog Analyzer sifts through volumes of log data and presents the information in simple, intuitive reports. However, it is practically impossible to manually keep up with the reports throughout the day, as they are constantly updated with the latest log data. EventLog Analyzer solves this problem with its real-time alerts feature. With this feature, you can:
- Get real-time notifications through email or SMS when any event of interest occurs
- Assign a program to be run upon alert generation.
- Categorize alerts into three priorities: high, medium, and low.
- Configure which device, or device groups, are to be monitored for the events.
- Provide additional parameters such as the specific users or domains that you want to trigger alerts.
- Specify how many times, and within how many minutes, an event should occur for the alert to be triggered.
- Choose from over 500 predefined alert criteria or define custom alerts.
- Be alerted for any compliance policy specific events.
- Receive alerts for custom correlations, such as when the correlation of two or more events calls for further investigation.
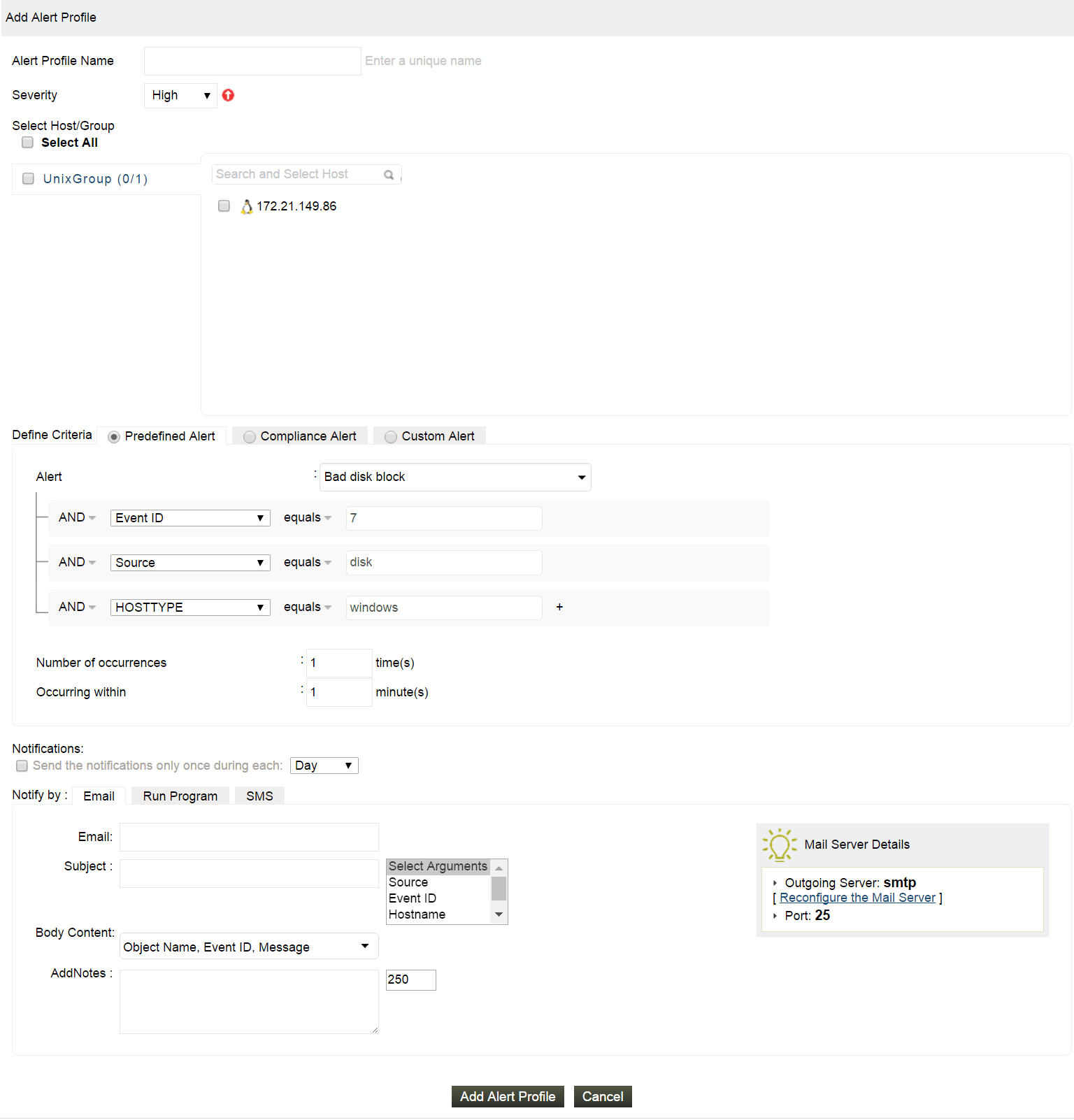

Predefined alert profiles
- EventLog Analyzer includes over 500 predefined alert criteria for Windows, Unix, applications, network devices, threats, and vulnerability scanners.
- Predefined alert profiles eliminate the need to create alerts for the most common events, saving the administrator time and energy.
Custom alert profiles
- Build custom alert profiles by defining all criteria from scratch, tailoring to your specific needs.
- Provide basic and advanced options.
Compliance alert profiles
- Compliance alerts are automatically triggered in case of any compliance policy -specific events.
- Include or exclude the events that pertain to your environment.
Correlation triggered alerts
- EventLog Analyzer allows correlations to be made between two or more events.
- Create rules for custom correlation alerts combining events from your routers, firewalls, servers, and other devices. These custom correlation alerts are highly accurate, as all events are validated with those from other devices.
Threat intelligence alerts
- EventLog Analyzer generates real-time alerts for known malicious entities interacting with your network.
- The latest threat intelligence is retrieved automatically from popular open source threat feeds on a daily basis.
- EventLog Analyzer starts scanning your network for threats as soon as you add devices for monitoring.
Other features
SIEM
EventLog Analyzer offers log management, file integrity monitoring, and real-time event correlation capabilities in a single console that help meeting SIEM needs, combat security attacks, and prevent data breaches.
IT Compliance Management
Comply with the stringent requirements of regulatory mandates viz., PCI DSS, FISMA, HIPAA, and more with predefined reports & alerts. Customize existing reports or build new reports to meet internal security needs.
File Integrity Monitoring
Monitor critical changes to confidential files/folders with real-time alerts. Get detailed information such as 'who made the change, what was changed, when and from where' with predefined reports.
Reporting console
Get 1000+ predefined reports for Windows, Unix/Linux, applications, & network devices environment that help to meet security, auditing, & compliance needs. Build custom reports for specific needs at ease.
Log management
Centrally manage collect, analyze, correlate, and archive log data from sources across the network. Get predefined reports and real-time alerts that help meeting the security, compliance, and operational needs.
Log forensic analysis
Perform in-depth forensic analysis to backtrack attacks and identify the root cause of incidents. Save search queries as alert profile to mitigate future threats.
Need Features? Tell Us
If you want to see additional features implemented in EventLog Analyzer, we would love to hear Click here to continue