- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing More..
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing More..
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports More..
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing More..
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer More..
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
EventLog Analyzer provides several options to customize the reports. As per your requirement, you can create new custom reports with a new report profile. Apart from the new custom reports, the existing pre-built (canned) reports can be customized to suit your need. Using these custom or customized reports, log analysis is made easy for administrators, since the reports are pruned out for specific data.
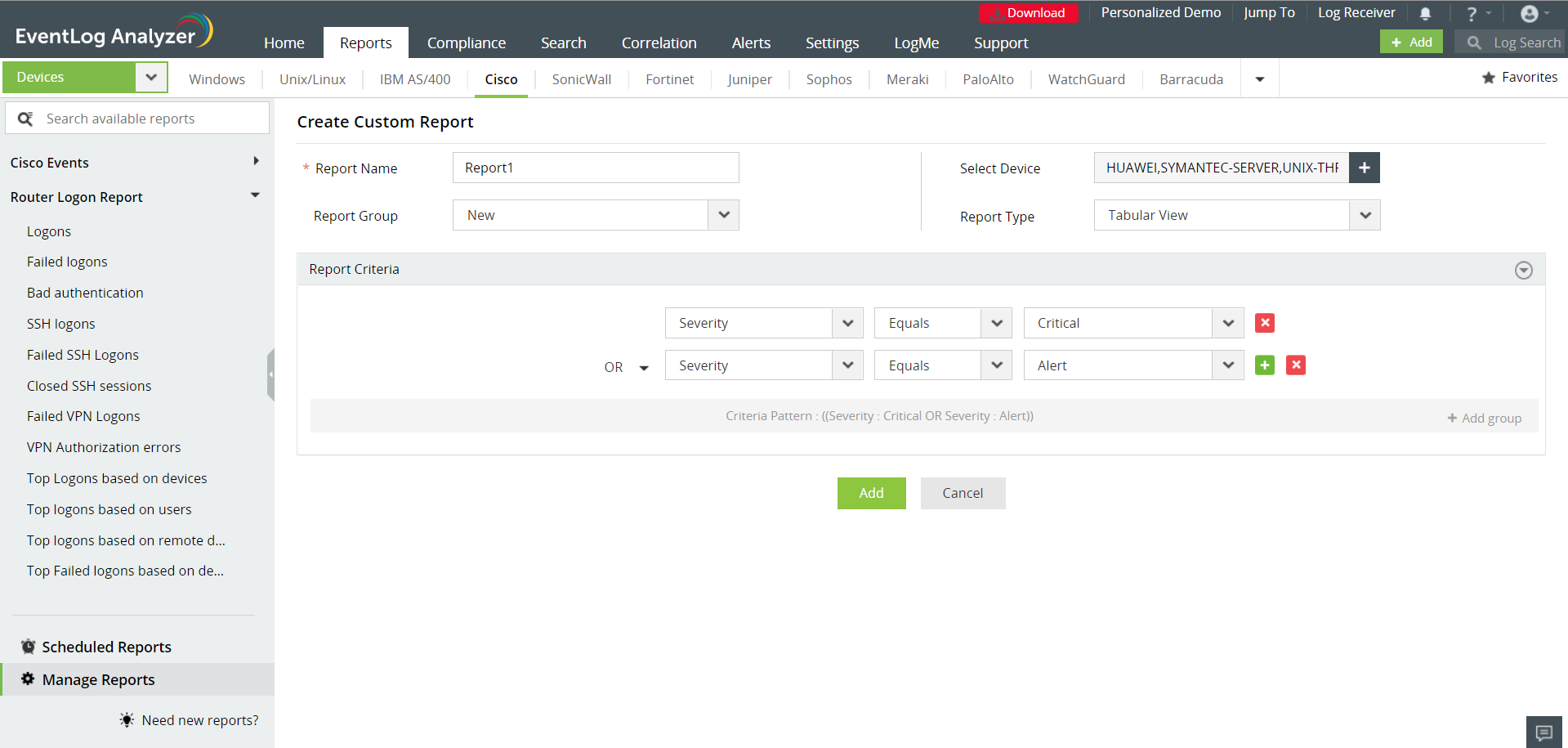
Custom Reports
Create new reports on event logs received from a select group of devices, based on specific event filters. Monitor critical servers exclusively, and set up schedules to automatically report on these parameters at regular intervals.
Customizing Existing Reports
EventLog Analyzer allows you to customize the reports. With this you will be able to modify the pre-built reports to suit your requirement. Instead of creating your own custom report, you can customize the existing pre-built reports, provided it suits your requirements.
Convert searches into alert profiles to quickly mitigate attacks
One of the fundamental components of an SIEM solution is its alerting tool. Real-time alerts give you complete control over the important events occurring in your network, so you can not only troubleshoot problems faster, but also handle security threats before they cause any real damage. In addition to real-time SMS and email alerts, EventLog Analyzer enables you to run scripts or execute custom workflows when alerts are triggered so you can start mitigating attacks right away.
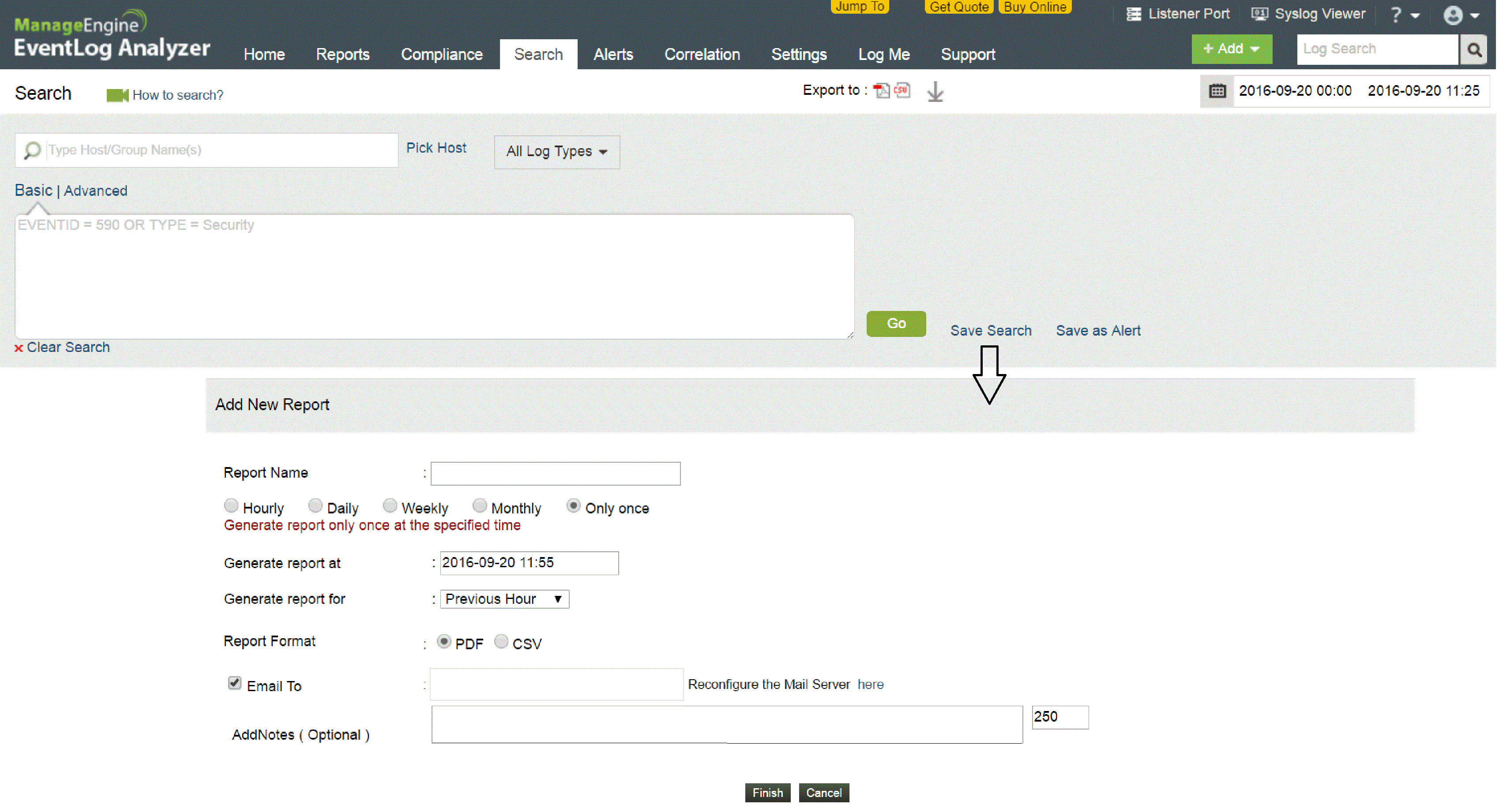
Every attack follows a pattern, and with EventLog Analyzer, you can capture this pattern in a search query and save it as an alert profile. That way, when a specified pattern of events happens in your network, you're alerted in real time. Stay on top of security events of interest to reduce the time it takes to detect and respond to a security threat in your security operations center.
Save a search query as an alert profile
Log searches enable you to drill down into a massive amount of logs and find what you need. With EventLog Analyzer, you can easily save your search query as an alert profile.
For example, say you type out the query A="x" and B="y" and C="z". You can save this search query as an alert profile so that when A="x" and B="y" and C="z" occurs in your network, you're notified in real time. This is a static correlation of events.
Get notified via email or SMS, or even choose to run a script when an alert is triggered. Tweak the trigger conditions, such as the number of times an event occurs within a certain time interval, so alerts are only triggered when you want them to be. Alert profiles are a fundamental part of using device logs to mitigate threats.












