- Free Edition
- What's New?
- Quick Links
- Log Management
- Application Log Management
- Application log monitoring
- IIS log analyzer
- IIS web log analyzer
- IIS FTP log analyzer
- IIS log parser
- VMware log analyzer
- Hyper V event log auditing
- SQL database auditing
- SQL server auditing
- MySQL log analyzer
- Apache log analyzer
- DHCP server auditing
- Database activity monitoring
- Database auditing
- Oracle database auditing More..
- IT Compliance Auditing
- IT Compliance Auditing
- SOX Compliance Audit
- GDPR Compliance Audit
- ISO 27001 Compliance Audit
- HIPAA Compliance Audit
- PCI Compliance Audit
- FISMA Compliance Audit
- GLBA Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- CCPA Compliance Reports
- CCPA Compliance Software
- NERC Compliance Audit Reports
- Cyber Essentials Compliance Reports
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
- PDPA compliance audit reports
- CMMC Compliance Audit More..
- SIEM
- Security Information and Event Management (SIEM)
- Threat Intelligence
- STIX/TAXII feed processor
- Server Log Management
- Event Log Monitoring
- File Integrity Monitoring
- Linux File Integrity Monitoring
- Threat Whitelisting
- Advanced Threat Analytics
- Security Log Management
- Log Forensics
- Incident Management System
- Application log management
- Real-Time Event Correlation
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Linux Log Analyzer More..
- Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Cisco Logs Analyzer
- VPN log analyzer
- IDS/IPS log monitoring
- Solaris Device Auditing
- Monitoring user activity in routers
- Monitoring Router Traffic
- Switch Log Monitoring
- Arista Switch Log Monitoring
- Firewall Log Analyzer
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet log analyzer More..
- Endpoint Log Management
- System and User Monitoring Reports
- More Features
- Resources
- Product Info
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Today's employees have become highly mobile—they work from home, in transit, or while they travel around the globe. Organizations also employ temporary employees, such as contract employees, who only work remotely. All of these people have to connect securely to their organization's networks using VPNs and it's important to monitor accesses to these VPNs, to ensure only authorized people are logging into the network. EventLog Analyzer is the ideal tool to help you achieve this.
Here's how EventLog Analyzer helps you proactively monitor VPN logs
Centrally collect and store VPN logs
EventLog Analyzer automatically collects logs from VPN devices and generates out-of-the-box reports and alerts for Cisco ASA, SonicWall, Fortinet, Huawei, Sophos, and Meraki devices. You can get a comprehensive overview of your VPN traffic and latency metrics with the help of the solutions centralized dashboard. The solution also offers location based VPN logon monitoring:
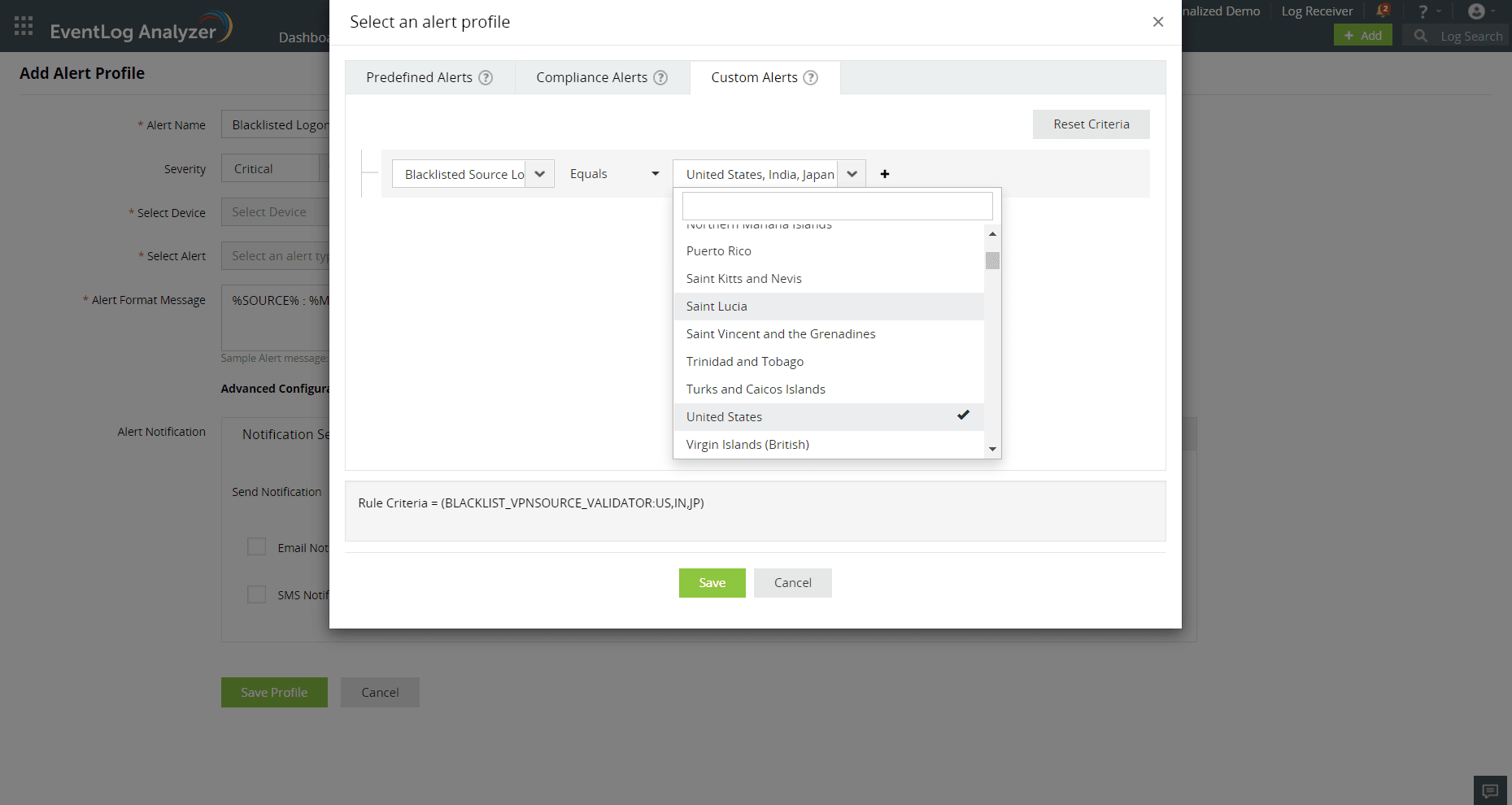
- You can create custom alert profiles to get notified on VPN logons based on locations.
- Add Blacklisted Source Location criteria and select locations of your choice.
- Visualize VPN logs with the customizable dashboard.
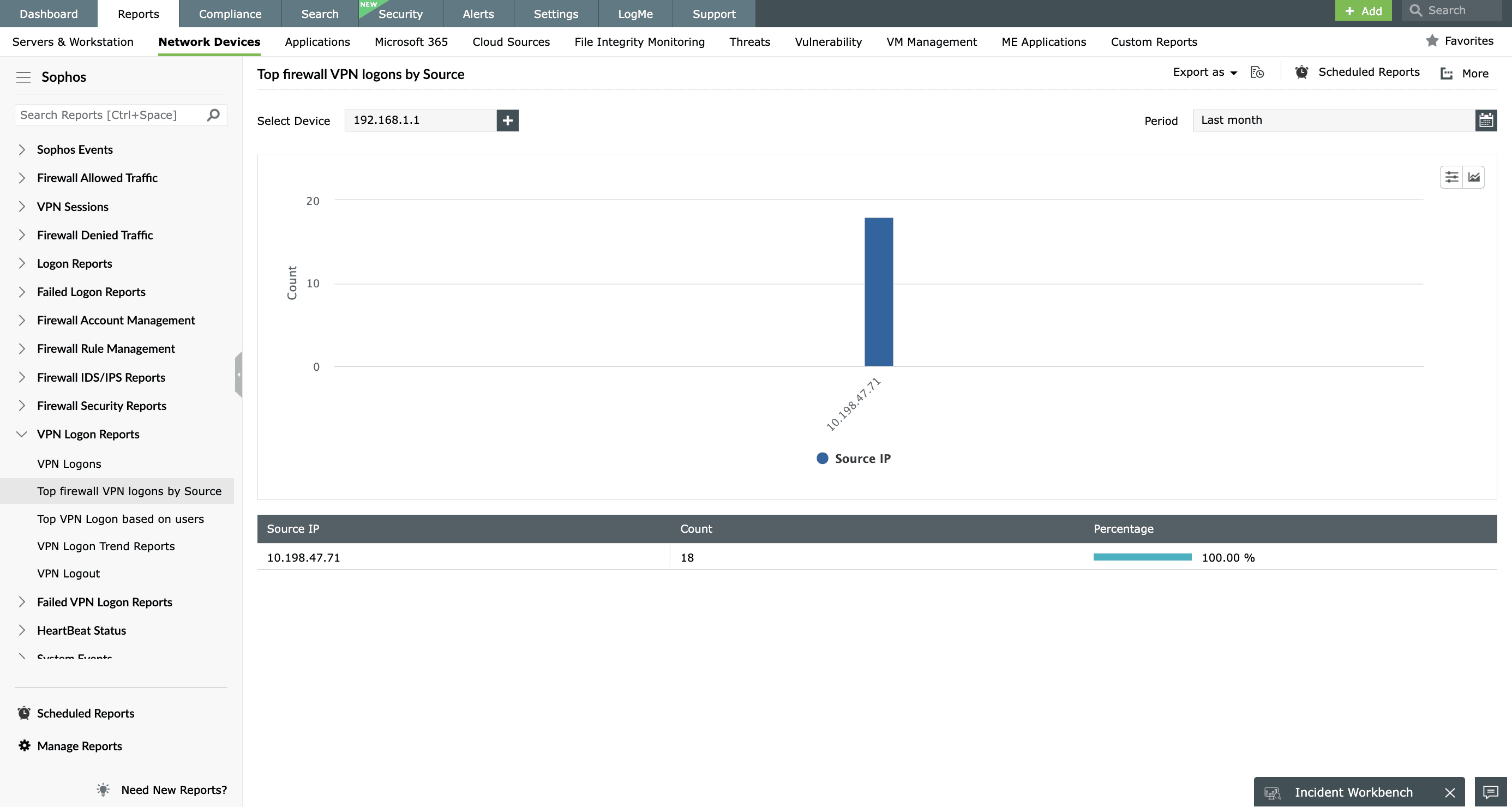
VPN monitoring with Sophos firewall
EventLog Analyzer helps you monitor VPN logs from Sophos firewall. Monitoring VPN logs helps you track activities of users who connect remotely to your organization's network. With EventLog Analyzer's out-of-the-box VPN reports, you can get insights into:
- Successful VPN logon attempts.
- Failed VPN logon attempts.
- Accounts with maximum VPN activity.
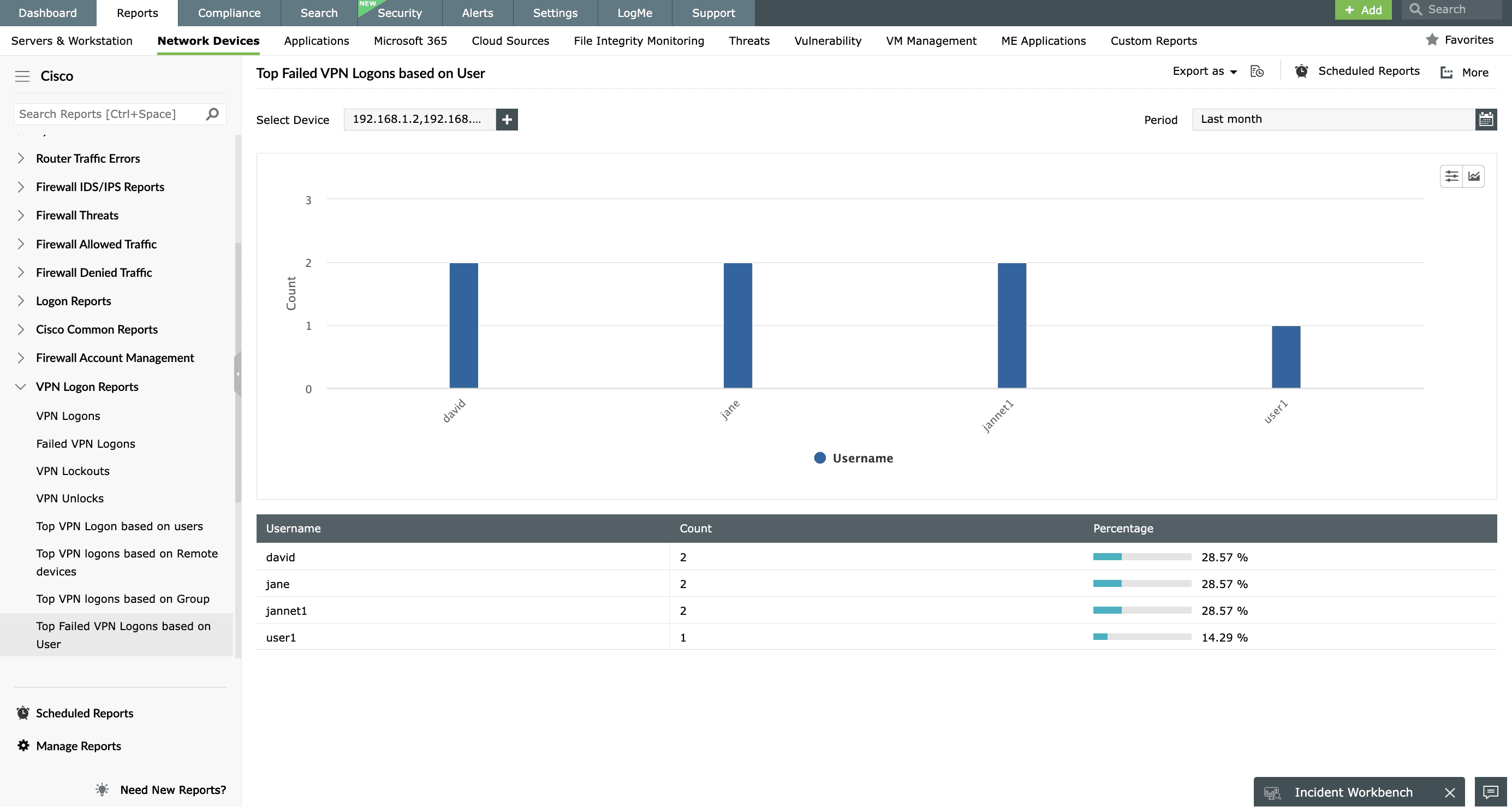
Cisco ASA VPN reports
EventLog Analyzer helps analyze Cisco ASA VPN logs, enabling a comprehensive review of VPN user activities. Its functionality extends to auditing VPN logins and discovering patterns in login behavior, offering critical insights into network anomalies and unauthorized access through VPN connections.
EventLog Analyzer provides intuitive VPN reports for Cisco ASA VPN logs, including:
- Cisco ASA VPN login reports: Track Cisco ASA VPN login history with reports on VPN logins, VPN lockouts, and more.
- Cisco ASA VPN user reports: Identify users who frequently login via VPN, review their details, and more.
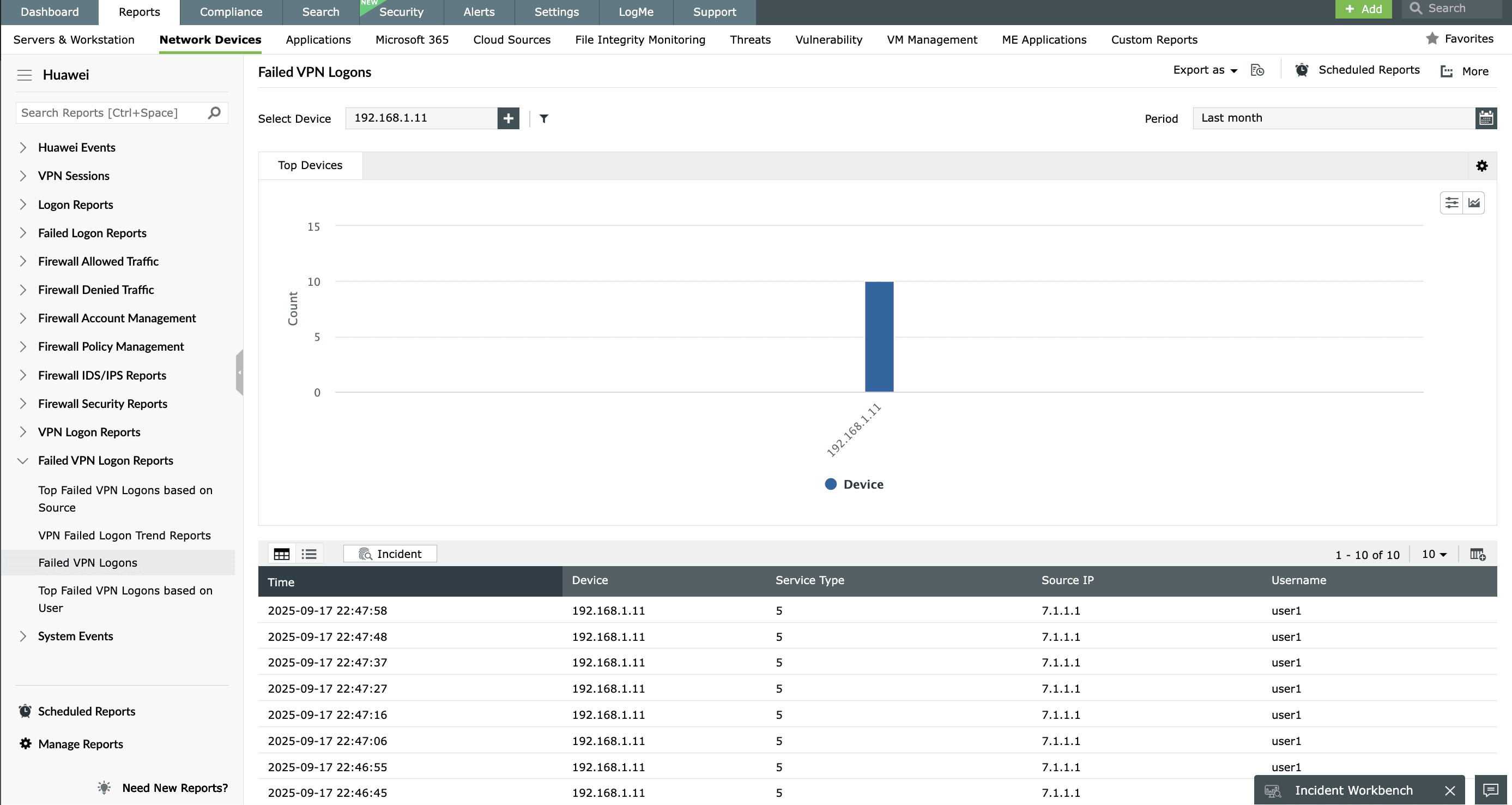
VPN monitoring with Huawei firewall
EventLog Analyzer keeps track of VPN connections established within your network. You can view details on the private IPs that get allocated most frequently, users who often use VPNs to get private IPs, remote IPs that often access the network, and much more. EventLog Analyzer comes with out-of-the-box VPN reports that get generated based on the VPN logs from Huawei firewall devices. The successful and failed VPN logon trend reports help identify anomalous activities, and patterns of successful and failed logon attempts over time.
Meraki VPN Reports
EventLog Analyzer's prebuilt reports for Meraki VPN provide comprehensive information on the most important aspect of VPN logons. There are exclusive reports for successful logons categorized based on devices and users. The trend report helps you understand the VPN logon trends in your network. You can customize reports by applying filters and drill down to raw log information straight from the reports. You can also export or schedule reports at your convenience, and set up email and SMS alerts as required.
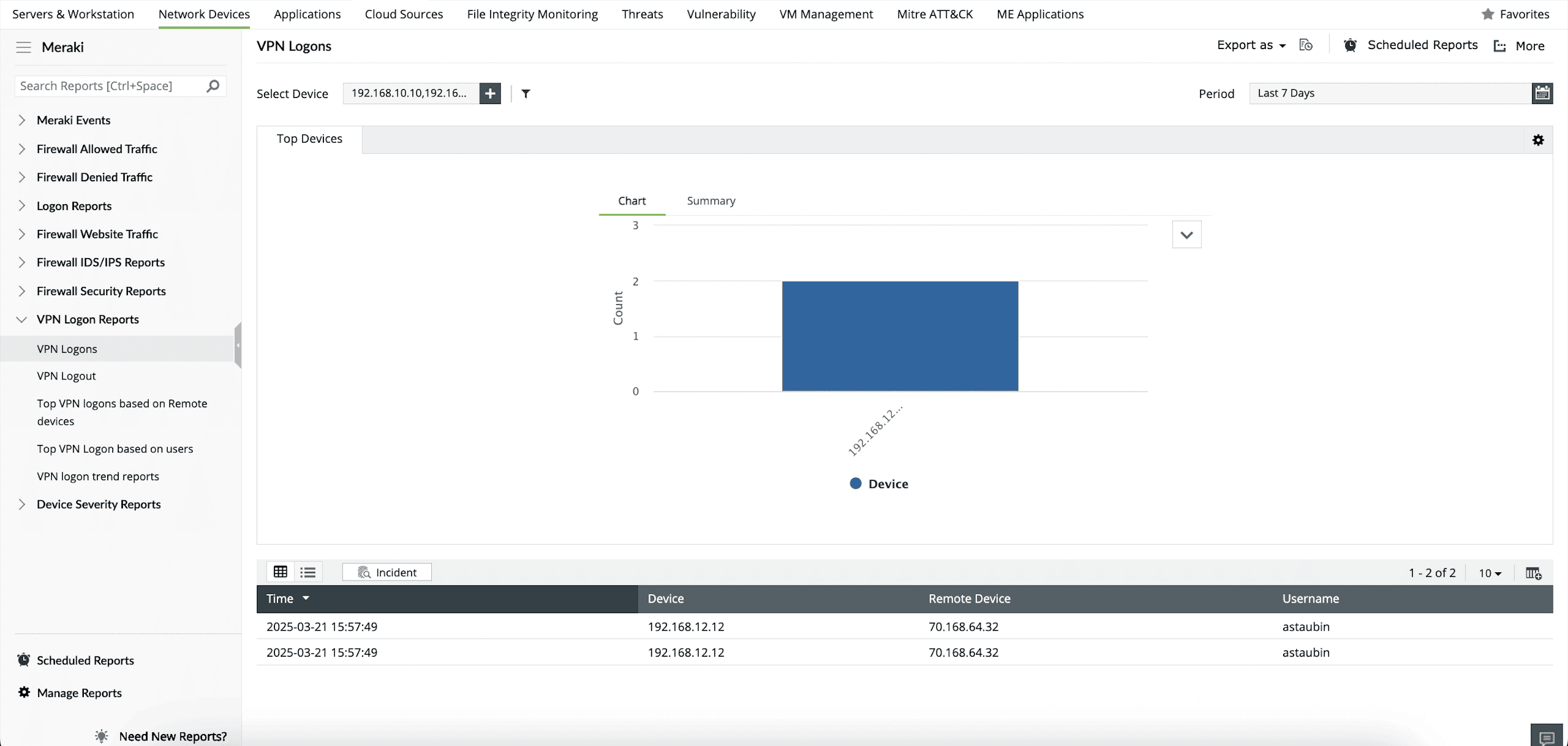
Fortinet VPN reports
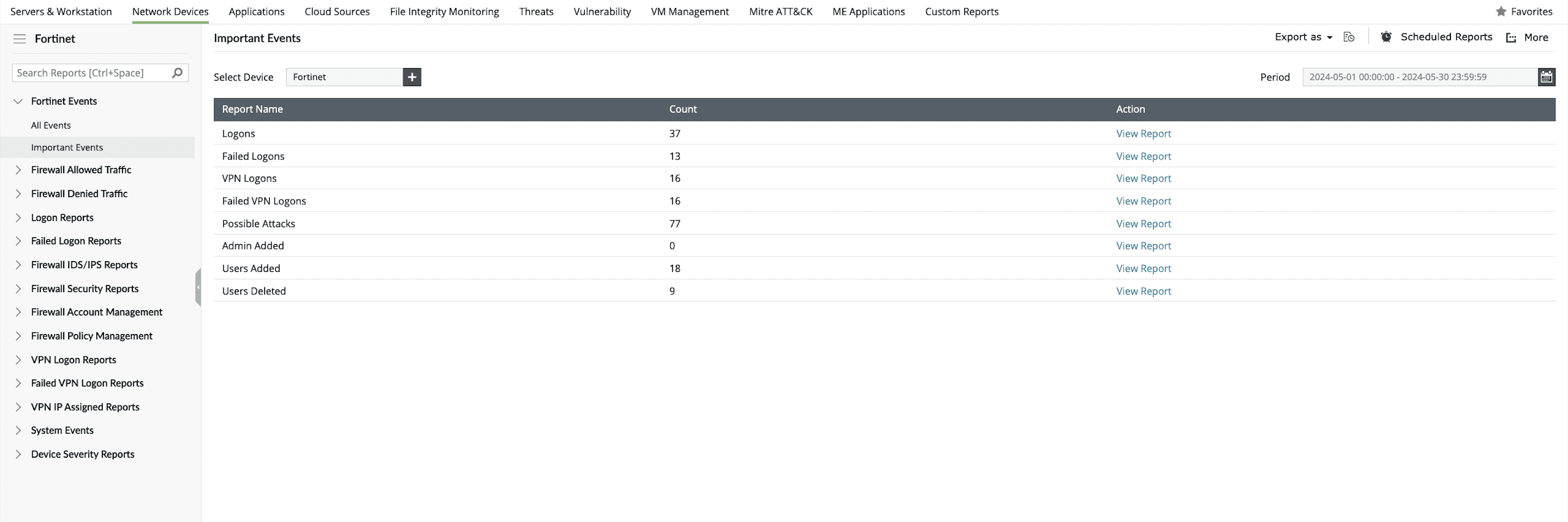
EventLog Analyzer serves as a valuable tool for monitoring VPN logs, ensuring that only authorized users gain access to your network, and fortifying your network security. Fortinet VPN reports provide information on successful and failed VPN logins. The top reports sort logins by device used and VPN user, so you can identify the users and devices that most frequently connect to your organization's VPN. The trend reports are useful in studying Fortinet VPN login patterns.
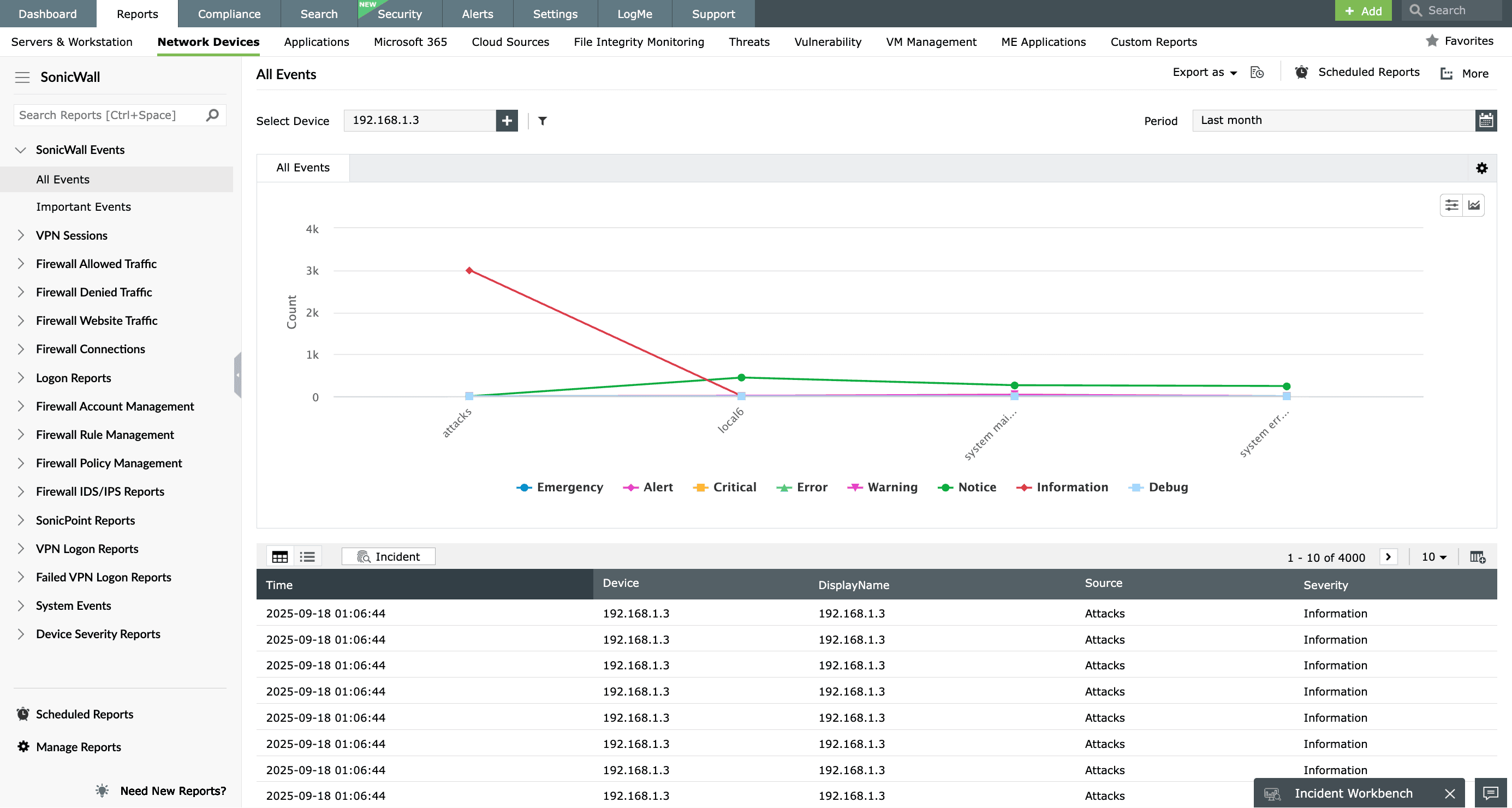
SonicWall VPN reports
Stay informed about network VPN logins and monitor VPN traffic in real time with EventLog Analyzer's VPN reports. You can also keep track of users who have logged in through a VPN, including the private IP addresses assigned to them. EventLog Analyzer provides complete VPN login monitoring for SonicWall VPN devices. View reports on successful and failed logins, VPN logoffs, and the top logins classified by source, device, and user. The trend reports offer extensive insights through visually intuitive graphs and charts, significantly elevating data visualization for effortless analysis.
Other solutions offered by EventLog Analyzer
IDS/IPS monitoring
Monitor IDS/IPS activities to proactively thwart malicious network traffic and generate real-time alerts when such activity is detected.
SNMP monitoring
Analyze SNMP traps based on severity level, to swiftly detect problems, troubleshoot network issues effectively, and identify potential security threats.
Database activity monitoring
Audit database server logs for MS SQL, MySQL, and Oracle to prevent unauthorized access, monitor account changes, and detect suspicious backup activities.
Web server monitoring
Monitor web applications like Apache, IIS, and DHCP logs and receive alerts on server usage, errors, and any attack attempts.
5 reasons to choose EventLog Analyzer as your VPN logging tool
1. Visualize VPN logs in an intuitive dashboard
Easily comprehend what's happening with your VPN, spot patterns, and find possible security issues using visual charts and graphs.
2. Monitor VPN logs for suspicious activities
Enhance your network security by monitoring remote users through VPN logs and accurately detect anomalies.
3. User Activity Monitoring
Gain insights into user activity and behavior within the VPN, helping you detect unauthorized access, data breaches, or insider threats.
4. Get real-time alerts and notifications
Trigger alerts in response to repeated failed VPN login attempts from a single source or if login occurs from unusual locations.
5. Integrated compliance management
Meet compliance requirements by generating compliance-specific reports, such as the GDPR, FISMA, HIPAA, PCI DSS, CCPA, and more based on VPN log data.
Frequently asked questions
VPN logs are records generated by VPN devices that tracks your user connections, authentication, session duration, traffic, errors, and security events. Network-to-network VPNs use certificates, while client-to-network VPNs use user authentication like usernames and passwords. VPNs use protocols like Internet Protocol Security (IPSec), OpenVPN with secure sockets layer (SSL), or Layer 2 Tunneling Protocol (L2TP) for encryption. VPN log plays a vital role in monitoring network activity, troubleshooting issues, and ensuring compliance with regulations.
VPN monitoring involves continuous tracking of firewalls and VPN devices to ensure private networks are secure from hackers. It also involves scrutinizing their availability, health, performance, and latency. Through vigilant monitoring of VPN traffic, you can ensure that data sent across your network remains encrypted and is swiftly transmitted. It also involves identifying major resource users and monitoring bandwidth usage.
Monitoring VPN logs is crucial for user analysis, situational awareness, foreign IP monitoring, and compliance. You can easily track any suspicious activity and optimize your network traffic with VPN log monitoring.
EventLog Analyzer serves as a robust VPN logging tool that offers out-of-the-box support for a wide range of VPN devices, facilitating real-time monitoring, alerting, and reporting. Its customizable features and comprehensive analysis capabilities empower you to enhance your network security, meet compliance requirements, and maintain the integrity of your VPN infrastructure.
Unleash the potential of VPN logs with EventLog Analyzer
EventLog Analyzer as a VPN log monitoring tool helps you:

- Review VPN user details and analyze trends in login patterns for various VPN devices with predefined reports to audit VPN logins.
- Ensure in-depth user analysis and behavior monitoring.
- Offer insights into browsing patterns and resource utilization during sessions.
- Encompass connection logs with login and logout information, timestamps, IP addresses, and usage.
- Leverage protocols such as IPSec, OpenVPN with SSL, or L2TP to encrypt data during transmission.
- Ensure compliance by tracking browsing patterns and application usage.












