Configuration items: The building blocks of your critical IT services
October 28 | 10 mins read
In today's digital age, an always-on IT infrastructure is no longer a luxury but a necessity for any successful business. But simply having a high-performant infrastructure isn't enough. To deliver essential IT services and ensure smooth operations, organizations need to keep close tabs on the building blocks of IT services, otherwise known as configuration items (CIs).
Essentially, CIs are the underlying components that contribute to delivering a service. Therefore, identifying, understanding, deploying, and managing CIs effectively is key to ensuring the smooth delivery and support of these services. Let's explore what CIs are and their importance in delivering IT services.
What are CIs?
Put simply, CIs are all the elements—including hardware, software, documentation, and even people—that make up your critical IT and business services. Just like a well-built structure needs strong bricks, your IT services rely on these CIs to function smoothly. By managing them effectively, you can help to ensure the reliable delivery of your IT services.
What are the types of CIs?
There are various types of CIs in an IT environment. They are broadly categorized as:

What are the key characteristics of CIs?
CIs play a crucial role in the delivery of services. Unmanaged or poorly documented CIs can disrupt service delivery or lead to failed change implementations.
By capturing and maintaining the key characteristics (see table 1), organizations can get a blueprint of how everything operates and relates in their IT environments. This information is of immense help when IT teams plan changes or respond to major incidents.
| Characteristics | Examples |
|---|---|
| TypeThe category of the CI. | Hardware: Servers, network devices Software: Applications, operating systems Documentation: User manuals, configuration guides Processes: IT service processes, change management People: IT staff assigned to manage CIs |
| Attributes Specific details that uniquely identify and define a CI | Hardware: Serial number, model number, location Software: Version number, license information Documentation: Title, author, revision date Processes: Process name, owner, documented procedures People: Name, role, contact information |
| Relationships Dependencies and connections between CIs. | A web application depends on a specific database server to function. Changes to the database server could impact the web application. |
| Life cycle status The current state of the CI in its life cycle | Active (in use), retired (no longer used), under change (being modified), planned for deployment (scheduled for future use) |
| Owner The person or team responsible for managing a specific CI. | A server administrator might own a physical server CI. A development team might own a software application CI. |
What is the difference between a CI and an IT asset?
All CIs are IT assets but not all IT assets are CIs.
If this distinction confounds you, here is how CIs and IT assets are different.
For instance:
- All servers are IT assets, but only servers critical for a specific service are configured as CIs.
- All software licenses are IT assets, but only licenses for service-related software are CIs.
Those IT assets that need to be managed closely to deliver a critical IT service, say your CRM, are designated as CIs. CIs typically offer a more granular view of the technical components that make up a service, including the interdependencies between different CIs that constitute a service.
An IT asset, on the other hand, is any element of your IT infrastructure that imparts value to your business and is managed from a financial standpoint. IT asset management typically involves the procurement, assignment, maintenance, and disposal of IT assets.
Both CIs and IT assets play vital roles in efficient IT service management. Here's a breakdown of key differences between CIs and IT assets:
| CIs | IT asset | |
|---|---|---|
| Focus | Technical details and configuration. | Financial and life cycle management. |
| Example | A specific server with its hardware and software details. | All printers owned by the company. |
| Relationships | Emphasis on relationships and dependencies between CIs. | Primarily standalone entities with basic relationship mapping (such as peripherals, networks, and owner). |
| Management purpose | Helps troubleshoot issues and understand service impact. | Tracks acquisition, cost, and disposal of IT resources. |
| Stored in | CMDB | IT asset management system |
| Life cycle | Managed throughout its life cycle to ensure service continuity. | May be disposed of or repurposed when no longer valuable. |
What is configuration management?
The primary goal of configuration management (CM) is to establish, control, and maintain the critical IT components that underpin IT services and applications. It also involves the creation and maintenance of an accurate database of all the configuration information of these components (i.e., CIs), so that reliable information is available for other ITSM practices such as incident management and change enablement.
This practice ensures that IT services built on these systems run reliably and as designed. CM achieves this through practices like creating, documenting, controlling, verifying, and maintaining CIs throughout their life cycle. Effective CM ensures a clear understanding of your IT environment.
Key CM activities include:
- CI identification and classification: The first step involves identifying all CIs within the IT environment and categorizing them by type, e.g., hardware, software, etc. This creates a comprehensive inventory of your IT assets.
- Collection and maintenance of CI attributes: Each CI should have a detailed record containing relevant attributes like model numbers, versions, configuration details, and ownership information. Regularly updating these attributes ensures accurate and up-to-date information.
- Relationship mapping between CIs: Understanding how CIs depend on each other is crucial. Configuration management helps map these relationships, allowing you to predict the potential impact of changes or failures.
- Configuration audits and verification: Regularly verifying the actual configuration of CIs against documented records helps identify any discrepancies. This ensures your documentation reflects the true state of your IT environment.
- CI life cycle management: CIs go through various stages throughout their lifespan, from initial deployment to modification, retirement, or decommissioning. CM processes track these life cycle changes, ensuring proper control and management at each stage.
How is configuration management related to CMDB?
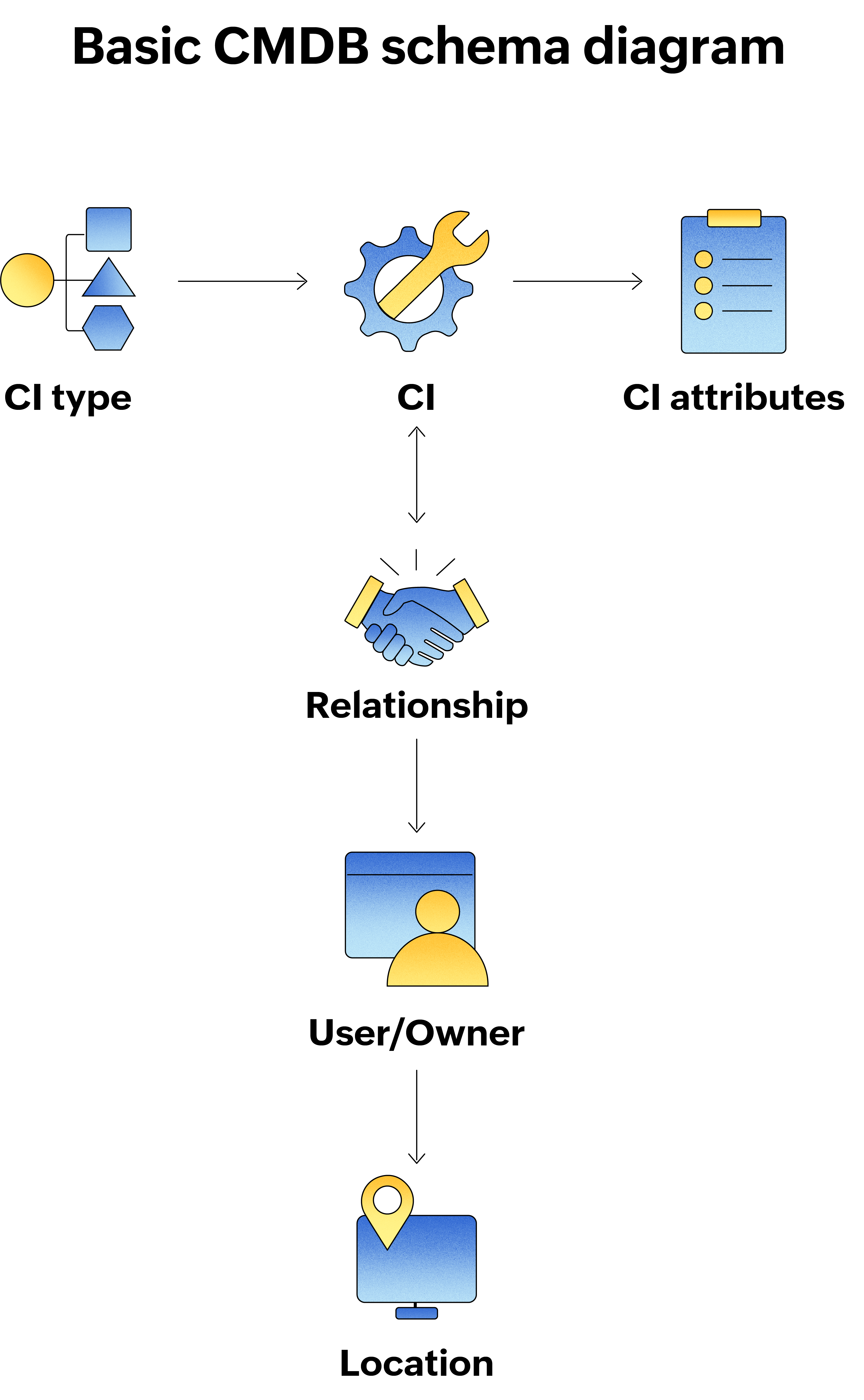
Fostering effective configuration management requires a powerful companion—the CMDB. Imagine the CMDB as the central nervous system of your IT infrastructure. It acts as a centralized repository, storing and managing all the crucial information about your CIs. Here's a basic schema diagram to understand how CI information is stored in the CMDB:
Use cases: The role of CIs in ITSM processes
1. Keeping flights on schedule: Zylker Airlines tackles a major outage
Scenario: A critical service outage disrupts Zylker Airlines' online booking system, grounding their operations. Frustrated passengers flood customer service lines, and Zylker's revenue nosedives.
In the midst of this chaos, Zylker's IT team springs into action, leveraging configuration management and the CMDB to perform the following.
- Rapid CI identification: Time is of the essence. The CMDB, Zylker's centralized repository for CI information, becomes a key source of information. By querying the CMDB, the team can swiftly identify all CIs that are part of the booking system, including servers, databases, network devices, and ticketing applications.
- Isolating the root cause: The CMDB not only stores information on individual CIs but also maps their relationships. This allows the team to analyze potential bottlenecks or failure points within the interconnected CIs that make up the booking system. This targeted approach significantly reduces the time needed to isolate the root cause compared to manually tracing connections.
- Tracking troubleshooting changes: As the team troubleshoots, they might need to make changes to specific CIs, like restarting a server or applying a hotfix. The CMDB provides a crucial audit trail, allowing them to track these changes in real time. This ensures a clear picture of the troubleshooting process and guarantees all changes are documented and reversible if necessary.
- Enhanced stakeholder communication: During a major incident, clear communication with stakeholders, including executives and worried passengers, is paramount. The CMDB empowers Zylker's IT team by providing accurate and up-to-date information. They can communicate the specific CIs impacted by the outage and the steps being taken for resolution. This transparency fosters trust and minimizes panic among stakeholders.
By effectively utilizing CIs and the CMDB, Zylker's IT team can diagnose the outage's root cause significantly faster. This allows for a targeted solution, minimizing downtime and getting the booking system back online quickly. Furthermore, the CMDB facilitates clear communication with stakeholders, ensuring everyone is informed throughout the incident resolution process. This not only minimizes business impact but also helps maintain Zylker Airlines' reputation for reliability.
2. Keeping the games running smoothly: Change management at Zylker Games
Scenario: Zylker Games, a leading online gaming company, is constantly innovating to enhance the player experience. This often involves changes to its IT infrastructure. Here's how CIs play a vital role in Zylker's change management process:
The development team has implemented server optimizations requiring a configuration change on a specific server.
- Impact assessment: Before implementing the change, the IT team uses the CMDB to assess potential impacts. By analyzing relationships between CIs stored in the CMDB, the team identifies all dependent CIs, such as game application servers and user authentication services. This allows them to evaluate potential disruptions to these dependent CIs.
- Verification and documentation: Following the impact assessment, the change is implemented on the target server. The CMDB again proves valuable. By verifying the configuration details on the CMDB after the change, the team confirms successful implementation. Additionally, the CMDB serves as a central repository to document the change details, including rationale, implementation steps, and personnel involved.
- Rollback procedures: The CMDB stores the previous configuration of the target server. If unforeseen issues arise, the IT team can leverage this information to quickly revert the server to its previous configuration, minimizing downtime and ensuring business continuity.
By effectively utilizing CIs and the CMDB, Zylker can implement changes with confidence. The ability to assess impact, verify successful implementation, and ensure rollback procedures minimize disruptions to critical gaming services. This allows them to continuously improve their platform while maintaining a good player experience.
Conclusion
CIs play a vital role in the overall health and functionality of your IT infrastructure. By effectively managing them, you lay the groundwork for a highly reliable, always-on IT estate. A comprehensive understanding of CIs empowers proactive problem solving, efficient incident resolution, and ultimately, superior service delivery—a critical advantage in today's digital landscape.
Investing in a robust ITSM tool with CI management capabilities and a powerful CMDB empowers your IT team to build a strong foundation for your organization's digital success, mitigating risks and fostering a proactive approach for other ITSM practices.
About the author

